he self-storage industry continues to evolve rapidly as more storage operators and vendors enter the market. According to a report from Mordor Intelligence, the estimated value of the global self-storage market was around $48 billion in 2020. The estimated value of the market in 2027 is $64.7 billion1.
The growing market size allows us to rethink how we approach critical aspects of self-storage operations, including security hardware, software, and processes. Having only padlocks, fences, and managers nearby is not an adequate security strategy any longer. As storage enterprises have grown and customer expectations have changed, storage operators must think beyond their site’s perimeters when devising a security strategy. Investing in equipment that provides layers of security and numerous fail-safes is critical for any self-storage operation. Some opportunities for adding layers of security include:
- Incorporating keypads at access points to enter buildings or restricted areas, such as boat and RV parking areas near their unit.
- Zone control – Leveraging an access control-enabled elevator or door so tenants can only access the areas near their units.
- Adding motion-sensitive lights and high-resolution cameras to the hallways.
- Offering door alarms and electronic smart locks for individual, unit-level security.
- Offering to equip high-value items like boats and RVs with motion-sensitive alarms.
Technologies that enable self-storage owners to implement a layered security approach include motion detection, electronic smart locks, and even AI-enabled video surveillance. There are many hardware and software components available to self-storage owners and operators; it can be hard to determine what security solutions work best for your operation when there are so many options available.
As you evaluate the security solutions available, you need to have a security strategy in mind. You should also consider your budget constraints, seeking to maximize your return on investment, and the competitive landscape around you. Security is a top-of-mind concern for your tenants; you don’t want to be seen as the storage option with the lowest degree of security compared to your competitors. Below are some additional questions to consider as you devise your security strategy.
- Do you want remote monitoring capabilities for your operation?
- How will you notify your employees and tenants of potential security breaches?
- How do you want your security strategy to influence the customer experience?
- Will you have employees on site?
- Will you offer after-hours access to your tenants?
- What access control processes do you plan to automate?
- How automated do you wish your facility to be?
- What are the expectations of your tenants, or what do competitive facilities offer their tenants?
Answering these questions will help you determine your security strategy. Once you know the goals of your security strategy you can evaluate the vendors available to you. Locating a security vendor and integrator with years of experience in the industry is crucial as you position your self-storage operation for long-term success, because an experienced vendor knows the industry and how to tailor the security strategy to fit your operation’s needs. Security vendors should not take a one-size-fits-all approach to implementing their products. Each storage operation is different.
Even if the security providers have the technical ability to install the equipment, you should consider the overall value-add experience when selecting your provider. Here are a few factors to consider when choosing your security provider:
-
Shared goals – Does the integrator listen to your security concerns and align with your goals regarding site security?
-
Industry experience – Does the vendor have ample experience in the self-storage industry?
-
On-going relationship – Will the integrator install security components and then disappear? Have they ensured the system runs well?
-
Ready to Scale – Has the individual set the system up so that there is room to scale as your business grows?
-
Integrable systems – Does the vendor only install specific security components, or do they offer a complete security system? Does the access control software integrate with your property management software?
-
Industry standard credentials – Does the integrator have the appropriate training and certifications Do they follow industry-standard protocols, or are some of their certificates outdated?
After you have determined your security strategy and selected a trusted vendor, you must evaluate the security components your site needs.
After you have determined your security strategy and selected a trusted vendor, you must evaluate the security components your site needs. Consider how the parts function individually and as a comprehensive system. The components you choose should all work together to ensure your operation functions optimally and provides an excellent experience for you and your tenants.
Secure The Perimeter
The gates and fences of a self-storage facility make up the first layer of security. You want to create a secure border. Broken fences and gates make your facility vulnerable to vandalism, break-ins, and disgruntled former tenants who could easily access the property unbeknownst to you.
In addition to discussing the different materials and types of gates and fencing available, you will want to consult an expert to ensure that your gate operator fits your operation’s needs. There are several gate types, including slide gates, vertical gates, swing gates, and pivot gates. You’ll want to consider your tenants’ needs and expectations when selecting the gate type. For instance, a site housing boats and RVs likely needs a different gate solution than a non-specialty storage site because maneuvering these high-value vehicles can be particularly challenging. You want to minimize the risk of damaging the gate and the vehicle when tenants enter the storage area. Typical weather patterns at your location may also influence your decision. Again, it is important to consult experts in the industry as you evaluate your options.
Access Control
The next line of defense is your site’s access control system. This system needs to quickly let paying tenants in the site and keep delinquent tenants and other unauthorized individuals out of it. Having a strong access control system is a crucial element of your security strategy and broader operations strategy.
- Keypads: Keypads should be top of mind when you think of access control. You should place keypads at all entry and exit points in your facility. It is also wise to put a keypad on every floor of a multistory facility. If you offer specialty storage options like boat and RV storage, putting a keypad at the entrance of the specialty storage area is recommended. With recent technological advancements, there are more options available than the standard numeric keypad. Integrating numeric keypads with Bluetooth technology creates a simple but secure way for tenants to enter your property. Encouraging tenants to create longer PIN codes than the minimum of four digits also enhances your security protocols.
- Cloud-based software: Moving your facility from desktop-based to cloud-based access control software will also enhance your site’s security. Cloud-based software is built to scale in ways its desktop counterpart cannot support. For example, cloud-based software can integrate with your property management software and unit security devices to automate the overlocking process, saving your operation valuable time. You can monitor the site remotely and get real-time notifications for any security event. Moreover, cloud-based software gives you access to a wealth of reports and analytics that can help you improve your operation. Even if the internet fails, a site controller with cloud-based software capabilities will allow you to perform some actions offline so your business doesn’t come to a screeching halt. We will cover the analytics and access control capabilities more in-depth later in this section.
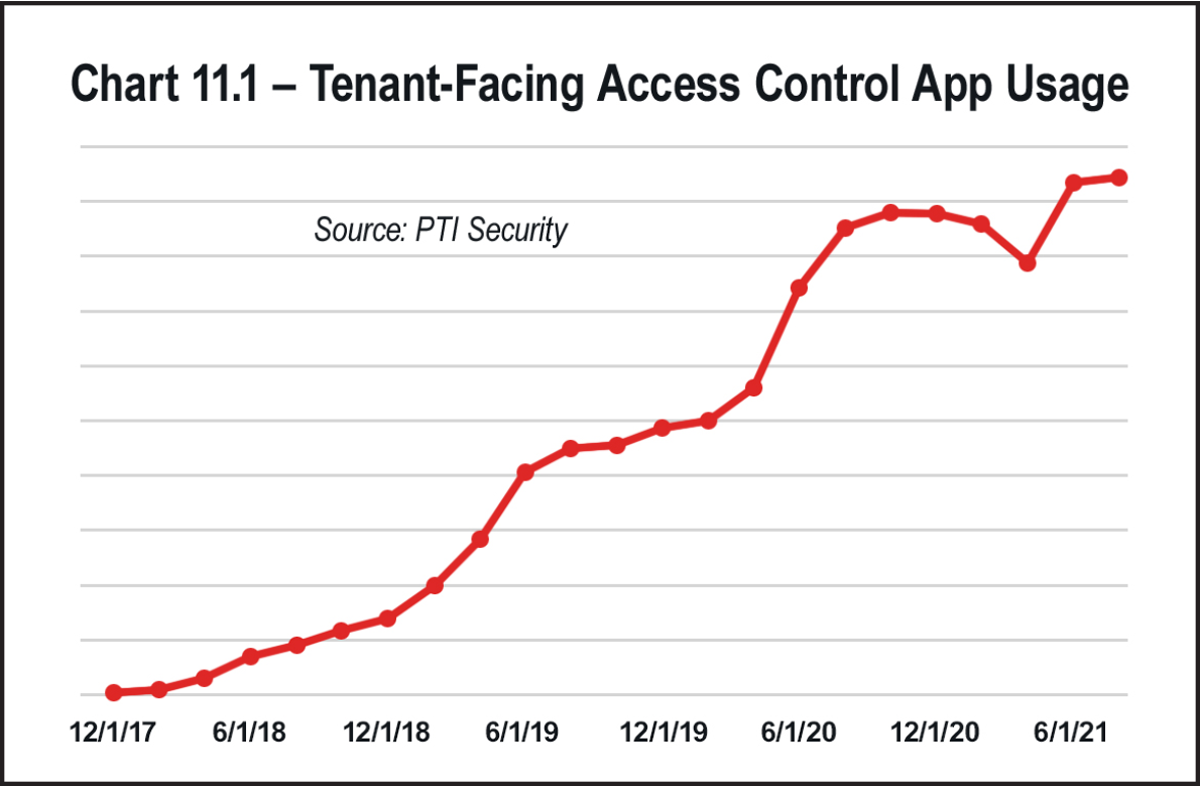
- Mobile access: Mobile access apps are now a standard feature in leading self-storage facilities. PTI has seen this type of app usage grow an average of 168 percent every year since launching its first version in 2017 (see Chart 11.1). Equipped with an integrated mobile app, authorized tenants can access areas of the property without using a code, key fob, or swipe card. Mobile apps also enable digital key sharing, where a tenant can give a friend a one-time encrypted key to their unit. Of course, site managers can deny the key share if they suspect foul play. Bluetooth technology also enhances the mobile access solution by opening the access points within a certain radius. You don’t have to worry about tenants opening their units when they aren’t on the property. Site managers can also use an operator-facing mobile app like StorLogix Mobile to monitor gate access and check critical reports. Incorporating a mobile app into your access control strategy increases your operation’s security and elevates your customer experience.
In addition to gates, fences, and an access control system, video surveillance should be a part of your security strategy. Not only do the cameras provide visibility across your property, but they also act as a deterrent to crime. Placing cameras around the perimeter of your property and throughout the corridors will help you track the activity on your site and reassure tenants that their valuables are secure.
You can also employ AI-assisted video cameras. The software can automatically alert operators of security concerns (like detecting movement in restricted areas). Some AI-enabled software can even notify the police if needed. Pinhole cameras at various entry points are another option. Moreover, many aspects of video surveillance can be automated; you may also choose to outsource your video monitoring. You don’t need to hire someone to watch the cameras all day to have a secure site. Placing lights near the cameras will provide a clear picture of site activity as well. Bad actors naturally want to avoid well-lit areas. Additionally, having good lighting and cameras is critical for tenants who have permission to access the facility after hours. If tenants wish to retrieve their RVs before sunrise, they expect to feel safe during their visit. Think critically about where you need to place lights and cameras to prevent crime and reassure tenants of their safety.
It may be tempting to skimp on the cameras or not prioritize fixing them when they break in the hope that the visual of the camera is enough to deter crime. However, crime attempts are inevitable at any facility, regardless of how much you invest in your security strategy. Select high-resolution cameras that clearly identify people and license plates, so you can quickly resolve security incidents.
Unit Security
Another layer of your security strategy must include unit-level security. The simple door and padlock combination is easy to bypass. Remember, security is a primary concern for your tenants. Knowing that you provide more unit-security measures than the standard padlock will give your customers peace of mind that no one will steal or damage their valuables.
Smart Locks
Electronic smart locks are an excellent unit security solution. Some examples of electronic smart locks include electronic overlocks and Bluetooth-enabled padlocks. The overlocks can sync with your access control software to engage the moment tenants are late paying their bills. It can also alert management if the lock gets damaged. Moreover, Bluetooth padlocks leverage smartphones and mobile apps to access the unit, eliminating the need to carry a physical key or remember a PIN. In the near future, the biometric ID technology we are accustomed to using to access smartphones will enter the self-storage market. Biometric-enabled locks are already present in the wine storage market.
Portable locks (typically padlocks) have remained a constant in self-storage and are often used for operators who need a solution that can be moved from unit to unit. Historically, these locks are used for overlocking units for tenants who are late in payment or for those existing facilities where running wires could be cost prohibitive and/or have traditional latches on doors of the facility. Today’s portable locks, like PTI’s Helox Smart Padlock, are more advanced and provide operators the ability to do contactless rentals through cloud-based access control as well as a more pleasant tenant experience that leverages Bluetooth connectivity, which is rapidly becoming an expectation of tenants.
Door Alarms
Door alarms are another aspect of unit security to consider. Just like electronic smart locks, door alarms can communicate with your access control software so you can know of the security threat instantly. Syncing the alarm with lights and sirens will also deter intruders and alert you to the threat in the office or be paired with sirens/lights/etc. to scare off intruders and alert anyone in the area.
In-Unit Monitors
Theft is a problem for any self-storage operator, but it can be partially, if not completely, mitigated by combining the aforementioned security solutions with an in-unit monitor such as StorageDefender. Such monitoring typically provides both operators and tenants activity alerts sent directly to the owners’ smart devices whenever any activity is detected in the unit. While this additional layer of security may not be for every facility, operators should know it is an option that can typically be an additional source of revenues for tenants who demand additional security.
As self-storage operations grow, owner-operators must consider how to monitor their security systems to drive business decisions. Advanced access control software and controllers, such as PTI’s next-gen CloudController and StorLogix Cloud platform, should be able to represent key performance indicators visually and generate customized reports so self-storage owner-operators can make effective business decisions without getting overwhelmed by all the data available to them. Then, they can analyze the data to identify the strengths and weaknesses of their operations, moving them to take actions that will ultimately drive revenue and enhance operational efficiencies.
PTI’s StorLogix Cloud access control software and CloudController work together to enable the following2:
- An Aggregated Dashboard
- Access at-a-glance intel on site activity and security equipment statues.
- Portfolio-wide visibility allows you to access this data from anywhere for all your facilities.
- Geographic site mapping visually represents the security health of all your facilities.
- Fully customizable reports help you track the KPIs that matter to your business.
- Complete Accessway Control
- Remotely control your site’s accessways and doors with one click.
- Open, lockdown, or hold open access points so you can respond to emergencies quickly.
- Fully Customizable Notifications
- Identify the notifications you want to receive without getting bogged down by the notifications you don’t need.
- Receive the notifications in the way that works best for you and your team, whether it is via text, email, browser, or push notifications.
- Receive all notifications in real time so you never miss a potential security incident.
- Leverage the notification data to generate granular reports and make better business decisions.
- Integration with other security products
- Mobile access solutions
- Unit security devices
- Property management software
Security technologies such as the CloudController and StorLogix Cloud will continue to advance the analytics capabilities and access control integrations in the future.
In summary, every security decision you make should align with your broader business and operations goals. Know how these security decisions provide value to your company. Remember to consider these questions as you determine the vision for your business:
- How does automation fit into your business vision and security strategy?
- How do you want to position your facility relative to your competition?
- How do you plan to track and analyze data to make better business decisions?
- What are your plans for growth in the next few years? Are the systems you’re putting in place today ready to scale?
Knowing the vision for your business and designing a security strategy that achieves this vision will drive success for your self-storage operation.
1 Mordor Intelligence. (2022). Self storage market trends, growth & industry analysis: 2022-2027 https://www.mordorintelligence.com/industry-reports/self-storage-market
2 Williams, M. (2022, October 10). Next-gen cloudcontroller improves self-storage security. PTI Security Systems. https://ptisecurity.com/next-gen-cloudcontroller-improves-self-storage-security/